Intro
I was reading about a kind of amazingly thorough exploit which could be done using a Raspberry Pi zero. Physical access is required, but the scope of what this guy has figured out and put together is really amazing.
Reading the description I decided is a good exercise in making sure I understand the underlying technologies. One was admittedly something I hadn’t seen before: DNS re-binding. That got me to reading about DNS re-binding, and that got me to looking at defenses against DNS rebinding.
HSTS to the rescue
Since in DNS rebinding you may have either a MITM (man in the middle) or a web site impersonated by a hacker, one defense against it is to use HTTPS. (The hacker will not have access to a web site’s private key and therefore has no way to fake a certificate). But what they can do is redirect users from HTTPS to HTTP, where no certificate is required.
HSTS is designed to make that move tip off the user by complaining to the user. Upon first visit the user gets a cookie that says this site should be https. Subsequent visits then are enforced by the user’s browser that the site accessed must be HTTPS.
drjohnstechtalk update
Two years ago I switched the default way I run my blog web site from HTTP to HTTPS due to the encryption offered by HTTPS, and the fact that search engines penalize HTTP sites.
It seems a natural progression in this age of increasing security awareness to up the ante and now also run HSTS. For me this was easy. Since I run my own apache server I simply needed to add the appropriate HTTP Response header to my server responses.
This is done within the virtual server section of the apache configuration like so:
# Guarantee HTTPS for 1/2 Year including Sub Domains - DrJ 11/22/16
# see https://itigloo.com/security/how-to-configure-http-strict-transport-security-hsts-on-apache-nginx/
Header always set Strict-Transport-Security "max-age=15811200; includeSubDomains; preload" |
Of course this requires that the apache mod_headers is included.
Results
I test it form a linux server like this:
$ curl ‐i ‐k ‐s https://drjohnstechtalk.com/blog/|head ‐15
HTTP/1.1 200 OK Date: Tue, 22 Nov 2016 20:30:56 GMT Server: Apache/2 Strict-Transport-Security: max-age=15811200; includeSubDomains Vary: Cookie,Accept-Encoding X-Powered-By: PHP/5.4.43 X-Pingback: https://drjohnstechtalk.com/blog/xmlrpc.php Last-Modified: Tue, 22 Nov 2016 20:30:58 GMT Transfer-Encoding: chunked Content-Type: text/html; charset=UTF-8 <!DOCTYPE html> <html lang="en-US"> <head> <meta charset="UTF-8" /> |
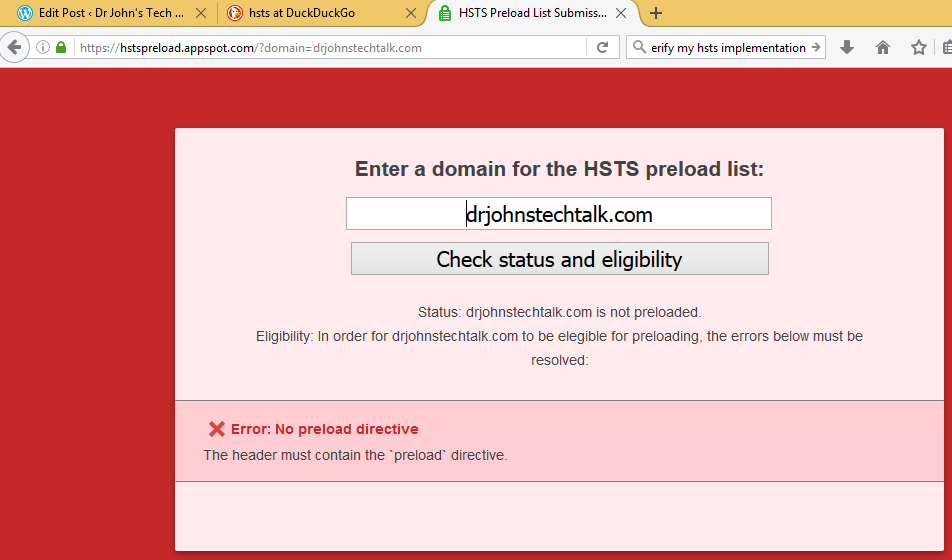
See that new header Strict-Transport-Security: max-age=15811200; includeSubDomains; preload? That’s the result of what we did. But unless we put that preload at the end it doesn’t verify!
References and related
drjohnstechtalk is now encrypted – blog posting from 2014
This site has a good description of the requirements for a proper HSTS implementation, and I see that I missed something! https://hstspreload.appspot.com/
You can’t run https without a certificate. I soon will be using the free certificates offered by Let’s Encrypt. Here’s my write-up.