Intro
I develop simple 3d objects using an approach which could be called 3d-object-as-code. The language is Openscad, and my few objects are all documented here: 3d printing some parts for the house. But that was started long before generative AI took off. So it was incumbent on me to explore what assistance I could get from use of chatgpt.
The details
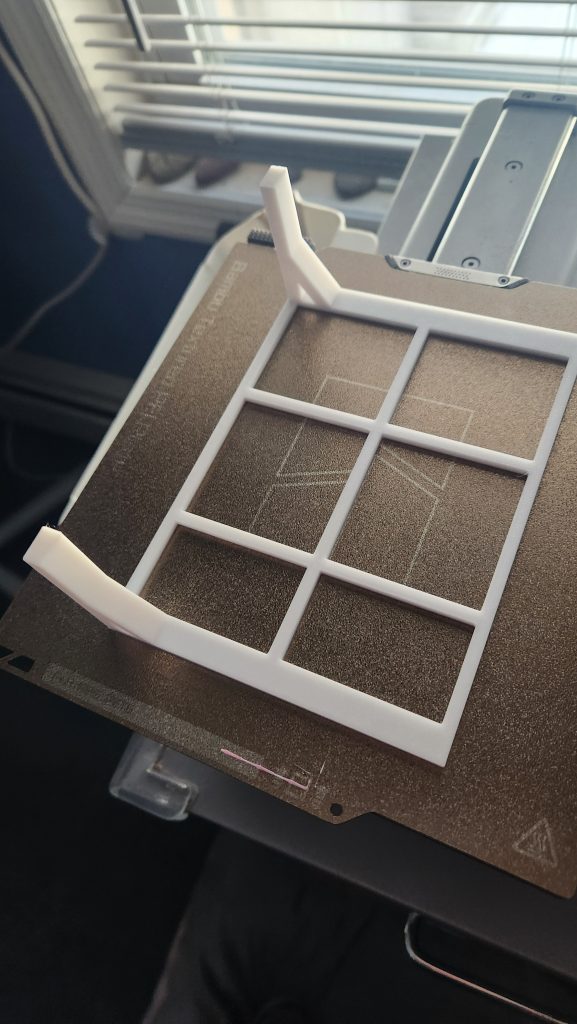
I wanted an object which would push against our utensil holder to pin it in place within the kitchen drawer, and at the same time make that space available for additional kitchen gadget junk. The final picture is further down below. I started having chatgpt generate the base based on my desired dimensions. So far so good. Then I had it re-do it using less material by making the base a lattice. Things already begin to fall apart. It dropped two of the ends though it did create a lattice pattern.
Now mind you no serious developer would proceed as I have done. I get the code from chatgpt, and paste it into the openscad app to render it to see what it created. Very indirect and inefficient! But this is just for me, so why not…
So anyway, I add the missing side by hand.
A time saver?
Yes! At this point chatgpt has gotten me started. on my own, I get psyched out by decisions as to whether or not to created centered versions of cubes, etc, and my issue when doing it by hand is getting lost in translation, literally. I often find myself three translations deep, and it gets to be overwhelming to think it through. chatgpt unilaterally decided the initial cube would not be translated, so I went with that simpler approach, and that helped.
I think I did manage to get chatgpt to add the legs as well, so that was a help.
chatgpt was good at creating modular and therefore reuseable code which even had nice comments! It’s like looking at your colleague’s code who writes better code than you and picking up a few pointers.
But not after awhile
I realized I needed to stabilize those legs. But what words to use in the prompt? I’m not an engineer. I said something to this effect
Starting from this openscad code, add a small cross arm having the same thickness as the leg in order to anchor the leg more firmly (openscad code...)
The result was laughable as it produced a horizontal piece attached to the bottom of the leg on the one end and attached to nothing at all on the other!
Second attempt:
Starting from this openscad code, add a small brace having the same thickness as the leg in order to anchor the leg more firmly. It should begin at (0,0,20) and end at (20,0,15) (openscad code...)
Still, it ignored these very direct start and end directives. I tried once more with no better results.
I also tried an approach requesting to add a bracing triangle of material to help stabilize the leg, but it laughably added an extruded triangle along the whole length of the leg!
At this point clearly the ai was not acting like an assistant, but a text language generator. It had clearly zero idea what it was doing.
So at that point, it was time negative exercise, useful only for this blog post and to make me humbly admit I do not know how to get the most out of chatgpt.
Finally
I had to add those bracing bits by hand-coding that part. That involved a rotation, a translation and a difference. It could have been worse.
The final product
The code
// DrJ 1/2025. Parameters in mm
// Dimensions of the box
width = 110;
length = 150;
thickness = 3;
epsilon = 1;
brace_angle = 30;
brace_z = 20;
spacing = 53; // Spacing between the lines in the criss-cross pattern
line_thickness = 4; // Thickness of the lines in the pattern
leg_height = 53; // Height of the legs
leg_width = 6; // Width of the legs
leg_length = 10; // Length of the legs
//width = width – line_thickness; // correction
side_height = thickness; // Height of the side leg
side_width = width; // Width of the side leg
side_length = 10; // Length of the side leg
module leg() {
// Create a leg
cube([leg_width, leg_length, leg_height]);
}
module shave_cube(){
translate([0,-epsilon,thickness]){cube([side_width,side_length+2*epsilon,leg_height]);};
}
module leg_brace() {
// Create a leg brace
difference(){
translate([0,0,-brace_z]){rotate(a=[0,brace_angle,0]){cube([leg_width, leg_length, leg_height]);}};
shave_cube();
}
}
module side_leg() {
// Create a leg
cube([side_width, side_length, side_height]);
}
module criss_cross_pattern() {
for (i = [0 : spacing : length]) {
// Horizontal lines
translate([0, i, 0]) {
cube([width, line_thickness, thickness]);
}
}
for (i = [0 : spacing : width]) {
// Vertical lines
translate([i, 0, 0]) {
cube([line_thickness, length, thickness]);
}
}
}
// Create the criss-cross box
criss_cross_pattern();
// Add legs at two corners
translate([0, 0, -(leg_height-thickness)]) {
leg(); // Leg at the bottom-left corner
}
translate([0, length – leg_length, -(leg_height-thickness)]) {
leg(); // Leg at the bottom-left corner
}
// add stronger sides
translate([0, 0, 0]) {
side_leg(); // Leg at the bottom-left corner
}
translate([0, length – side_length, 0]) {
side_leg(); // Leg at the bottom-left corner
}
leg_brace();
translate([0,length – side_length,0]){
leg_brace();}
//shave_cube();
Conclusion
I got not-so-great results in my attempt to use the chatgpt o4 generative ai offered by Duckduckgo. The basic stuff, yes, it got me started and taught me how to make good modular openscad code. Anything remotely complex, forget about it. You want to treat ai like an assistant, right, but this assistant has near zero understanding of what I want and did not learn even after multiple attempts within the same chat session. It should be put out to pasture…
However, I am always willing to take the fall. I was just going by the seat of my pants with regards to prompt engineering. Maybe if I had chosen better prompts, or let ai have freer reign to do the whole design I would have experienced better results. But shouldn’t my “assistant” be better at understanding me?
References and related
All about Openscad: https://openscad.org/
The original post: 3d printing some parts for the house.
You can use chatgpt directly: chat.com or the way I used it, from the menu of https://duckduckgo.com/
The Etsy shop of the person who printed this for me for only $5: https://www.etsy.com/shop/gizmoswidgets