Intro
I was recently asked if a new certificate a web site is about to deploy would require any changes to our clients such as needing to import this certificate into their Java keystore.
The details
Well, I saved the certificate on a Linux server calling it my.crt and examined it using openssl:
$ openssl x509 ‐text ‐in my.crt
My greatest hits amongst the openssl commands are listed here: My favorite openssl commands
Anyway, the output begins like this:
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
68:5f:f8:b6:5e:56:c2:1d
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., OU=http://certs.godaddy.com/repository/, CN=Go Daddy Secure Certificate Authority - G2
Validity
Not Before: Apr 5 22:57:01 2018 GMT
Not After : Apr 5 22:57:01 2020 GMT
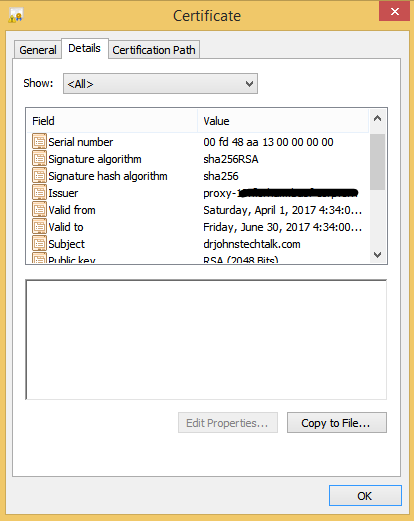
Subject: 1.3.6.1.4.1.311.60.2.1.3=US/1.3.6.1.4.1.311.60.2.1.2=California/2.5.4.15=Private Organization/serialNumber=C2417721, C=US, ST=California, L=Carlsbad, CN=www.drj.com
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public Key: (4096 bit)
Modulus (4096 bit):
00:da:c7:18:a2:4d:b5:c9:95:22:b0:64:50:e7:b8:
... |
So I checked the text after the Issuer field, C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., OU=http://certs.godaddy.com/repository/, CN=Go Daddy Secure Certificate Authority – G2
This is the intermediate CA. And it exactly matches their current certificate we already trust. So no problem, right, we are good to go, right? Not so fast grasshopper. This certificate contains a totally new element for us. I happened to notice it has a 4096 bit key length. Never seen that before though I have heard about it.
How do we even know our old browsers and even proxy server are going to be good with that? The best way I reasoned is simply to find another site with a 4096 bit certificate. Well, it took me almost an hour before I found one, and DDG and Google searches proved fruitless. I found it by taking logical guesses, as in, surely some security-minded organization has deployed these already??
ssllabs.com. Nope. godaddy.com. Nope. www.google.com. Nope. Gnupg.org, Nah, ah. Lets Encrypt. Also a no. Then I tried nist.org and found the weirdest thing. They send several certificates, one of which is *.bluehost.com which is 4096 bits. But it makes no sense being part of the certificates on nist.org, as an ssllabs.com server eval will tell you. So then I tried www.bluehost.com. Paydirt!
$ examinecert www.bluyehost.com
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
af:a7:b9:22:4f:d5:7e:6b:78:4b:5a:23:d0:35:50:23
Signature Algorithm: sha256WithRSAEncryption
Issuer: C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Domain Validation Secure Server
CA
Validity
Not Before: Oct 16 00:00:00 2015 GMT
Not After : Oct 17 23:59:59 2018 GMT
Subject: OU=Domain Control Validated, OU=Hosted by BlueHost.Com, INC, OU=PositiveSSL Wildcard, CN=*.unifiedlayer.co
m
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (4096 bit)
Modulus:
00:c5:2b:10:d2:20:bb:d9:1b:e1:d3:b2:d1:9b:6f:
... |
examinecert is a bash function I created defined as:
examinecert () { echo|openssl s_client -connect "$@":443|openssl x509 -text|more; } |
And for this company that brings up a host of questions. if their again IE 11 has never encountered a web site with this long of a key length, how will we know what will happen the first time?
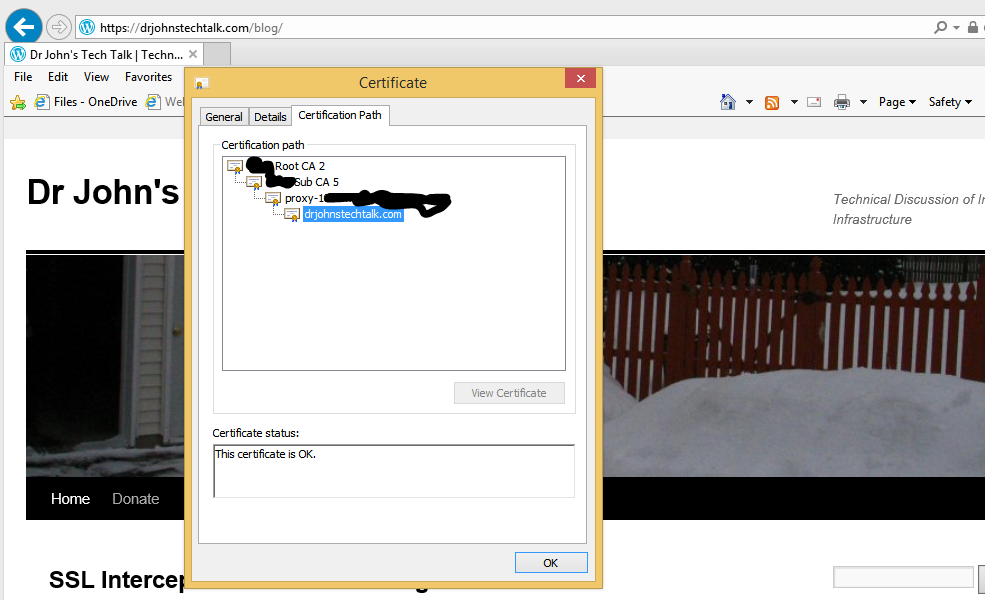
Also, some sites get SSL intercepted by Bluecoat proxy. How will that infrastructure handle it? Will it handle it?
That;s why it was so important to find a real-world example, as painful as that exercise proved to be.
The answers are somewhat surprising.
Yes, ancient Internet Explorer probably handles 4096 bit key lengths just fine. I actually haven’t fully tested that one yet.
But it doesn’t matter for this company. Their Bluecoat proxy intercepts the SSL. So, yes, that part works, and re-creates its own certificate, but issued as a standard 2048-bit key length! So that is what IE sees so I know there will be no issue there. I say surprising because usually the generated certificates so carefully preserve all aspects of a certificate: same expiration date, same common name, etc. Whether or not this key length reduction is configurable or not I have yet to find out.
Follow up
As a result of my prodding, badssl.com will include a 4096-bit certificate with which to test things out.
Conclusion
After an arduous search (I’m sure next year this time this will become much easier) we found a public site which can be used to test 4096 bit key lengths: www.bluehost.com. Obviously GoDaddy also issues 4096-bit certificates since that is what this particular web site uses as their issuer, but I have yet to find an actual live example of one.
Bluecoat SSL interception by default does handle this long key length, but generates its private version of it with only a 2048 key length, to our surprise.
Just remember, if you have a Raspberry Pi you can run all these commands that I’ve shown because you have a bone fide Linux system.
Case: closed!
References and related
This site has all sorts of SSL scenarios to test against: https://badssl.com/.
To jump straight to their 4096-bit CERT: https://rsa4096.badssl.com/